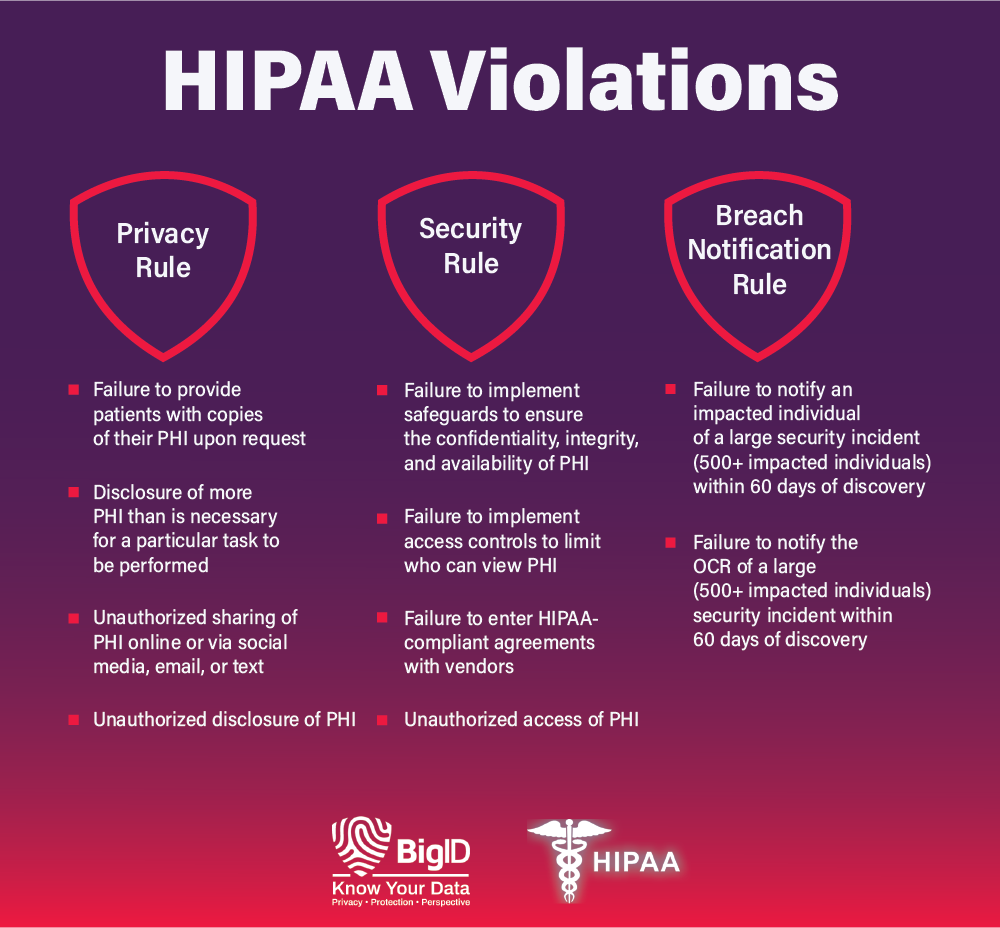
There’s devil in the details of the various controls organizations use to ensure compliance with the requirements of the Health Insurance Portability and Accountability Act (HIPAA). We highlighted them all in a recent blog post if you want to read more.
Broken out as administrative, operational or technical, HIPAA controls refer to the various processes, procedures and system features that help organizations minimize risk by detecting, reducing or even eliminating the probability of a certain threats.
Basically, administrative controls are those dealing with human behavior, while operational controls speak to the risks inherent to the physical environment or location. And technical controls focus on – you guessed it – technology, from the computing hardware to the wireless network and more.
A risk manager typically rates the effectiveness of each implemented control using a process maturity scale:
- Minimal – control is not fully implemented or is used in a way that requires reliance on individual discretion for its implementation.
- Repeatable – control is implemented in a consistent manner that can be repeated by different individuals and in different situations, although not all associated procedures may be formally documented.
- Defined – control is implemented and managed according to a standardized procedure that is well documented.
- Benchmarked – control is implemented using repeatable, defined methods that conform to industry best practices.
- Optimized – control is implemented using repeatable, defined methods that conform to industry best practices and which are routinely monitored to ensure control remains appropriate to a changing environment. At this level, controls are subject to continuous process improvement.
For an organization subject to HIPAA compliance, the controls can seem a bit daunting, and rightfully so, as they should not be taken lightly. At ZZ Servers, we help customers track more than 40 different processes, procedures and tests to gauge where they stand on the implementation of each of the 24 controls.
So how “optimized” does an organization need to be for a given control? And are any controls more important than others?
Recent headlines would suggest that device and media controls are among the hotter HIPAA items. Last month, it was revealed that wireless health services provider CardioNet reached a $2.5 million settlementwith the U.S. Department of Health and Human Services (HHS) Office for Civil Rights (OCR). It seems that a CardioNet laptop computer with electronic personal health information (ePHI) was stolen from an employee’s car.
In the ensuing investigation OCR reported that CardioNet did not have sufficient policies and procedures in place with respect to ePHI. In fact, those procedures were still in draft form and had not been implemented, much less optimized.
One can only wonder if CardioNet was somewhere above “minimal” on the process maturity scale for their device and media controls if the financial punishment would have been different for them.
But the larger point is that getting your HIPAA house in order is no small feat. And all of the controls are important.
Reaching “optimized” status across on any of the 24 HIPAA controls (and the 40 checklist items) is a tall order for smaller organizations, and that’s where ZZ Servers can help.
We specialize in building HIPAA-compliant systems backed by a full set of managed service offerings where security is built in from the beginning. ZZ Servers takes the security of your business and the protected health information data seriously, and we know security inside and out.
It’s this kind of mentality and expertise you want on your side to help you navigate the detailed controls and checklists that will boost your HIPAA compliance – without busting your budget.
Connect with us today and let us show you how we can help.