Are you aware of the potential risks linked to your business collaborations with third-party vendors and suppliers?
Performing thorough third party risk assessments is crucial to safeguard your business.
This guide will help with the strategies to effectively identify, monitor, and manage these risks. By doing so, you can protect your business from any potential threats and ensure the success of your partnerships with external entities.
Third Party Vendor Risk Management Programs Overview
- Third-party risk assessments involve analyzing vendor risk along the supply chain and identifying and evaluating potential risks.
- The assessment process includes identifying vendors, creating assessment questionnaires, examining and analyzing results, and taking action based on the findings.
- Best practices for third party risk assessments include establishing clear policies and procedures, involving relevant stakeholders, and documenting and communicating the assessment results effectively.
- Ongoing monitoring processes, periodic due diligence reviews, and addressing identified issues promptly and effectively are essential for effective third-party risk assessments.
What Are Third-Party Risk Assessments?
A third-party risk assessment evaluates and identifies potential risks associated with vendors and suppliers to mitigate potential issues. This assessment is a crucial component of a comprehensive risk management program. By conducting a thorough evaluation, you can effectively identify and assess the level of risk posed by third parties within your supply chain.
Third-party risk assessment is important for several reasons:
- Protecting Data and Intellectual Property: Organizations often share sensitive customer data, financial details, and intellectual property with third-party vendors. Without a comprehensive risk assessment, this data could be exposed to theft, breaches, or misuse.
- Operational Continuity: A vendor’s failure, be it operational, financial, or resulting from another risk, can disrupt an organization’s operations. Organizations can develop contingency plans and prevent operational downtime by assessing these risks in advance.
- Legal and Regulatory Compliance: Many industries have regulations that mandate certain standards for third-party relationships. Organizations might inadvertently breach laws without proper assessment and oversight, resulting in penalties, fines, or legal actions.
- Reputation Management: The actions of third-party vendors can reflect on the hiring organization. A vendor engaging in unethical or problematic behavior can tarnish the reputation of the organization that employed its services.
- Financial Implications: Financial risks associated with third parties can range from unexpected costs due to poor contract management to more significant implications like fraud or financial loss if the vendor goes bankrupt
- Strategic Alignment: Ensuring third parties align with the organization’s values, ethics, and strategic goals is vital. A misalignment can lead to conflicts, inefficiencies, or public relations issues.
Third-party risk assessments allow you to develop a robust risk management strategy that addresses potential vulnerabilities and safeguards your organization. During the assessment, risks are identified and categorized based on severity and impact. This information is then used to prioritize risk mitigation efforts and allocate appropriate resources.
Third-Party Vendor Risk Assessment Process
Modern business management can’t do without vendor risk assessments. We live in a time where we often outsource work and partner with other businesses, it’s important to understand the risks that business partners may pose.
Let’s look into the details and best practices of the vendor risk assessment process to strengthen your business against unexpected vulnerabilities.
Identify Third-Party Relationships You Need to Assess
Identify the vendors that require assessment based on their potential risk levels.
To effectively manage third-party risk, it’s crucial to prioritize and assess vendors based on their risk levels. Here is a step-by-step process to help you identify the vendors that need assessment:
- Define the scope and objectives of the assessment: Establish what you goal is for the assessment.
- Gather relevant information about the vendors: Collect data on vendors’ cybersecurity measures, financial health, and reputation.
- Assess the identified risks and their potential impact: Analyze the risks associated with each vendor, considering financial and reputational risks.
- Document the assessment findings and recommendations: Create a comprehensive report detailing the assessment results and any necessary actions to mitigate risks.
Make a Third Party Risk Assessment Survey
Creating a risk assessment survey is a great way to collect necessary information about your vendors for a thorough review. It’s a great tool for managing risks from third parties and understanding the possible risks of working with them.
The survey can help you collect data about a vendor’s security measures, ways they handle vulnerabilities, and their overall approach to risk management. It should look into different parts of the vendor’s operations, such as how they protect data, their ability to respond to incidents, and their adherence to industry rules.
This data collection allows you to gauge a vendor’s risk profile and decide on the right level of scrutiny needed. It lets you decide which vendors to work with and the necessary risk-reduction strategies to implement.
The risk assessment survey is a useful tool in the vendor assessment process and supplier risk evaluation. It helps you maintain control over your third-party relationships and defend your business from potential risks.
Have the Vendors Complete the Assessment
Once the risk assessment questionnaire is prepared, vendors can complete the assessment, providing you with valuable information about their security controls and risk management practices. This step is crucial in understanding and mitigating third-party risks.
Here are four key points to consider:
- Assessing vendor risk: By having vendors complete the assessment, you gain insights into their overall risk profile, enabling you to evaluate the potential risks associated with the third-party relationship.
- Identifying security controls: The completed assessment allows you to assess the effectiveness of vendors’ security controls. This helps determine if their practices align with your organization’s security requirements.
- Evaluating risk management practices: Vendors’ responses in the assessment provide valuable information about their risk management practices. This allows you to gauge their ability to address and mitigate potential risks effectively.
- Informing decision-making: The completed assessment is a crucial input for decision-making regarding vendor relationships. It helps you make informed choices about engaging with vendors and managing the associated risks.
Look at the third-party risk assessment outcomes to understand how well your vendors manage their security and risk. It’s really important to know about the risks when you work with suppliers.
You can spot possible weaknesses and issues by digging deep into the findings. This knowledge helps you create a thorough third-party risk management program that fits your risk profile. You’ll be able to handle third-party risk and compliance effectively, ensuring the right security measures are in place.
And don’t forget looking over and breaking down the results can help you spot any operational risks and deal with them immediately. This approach puts you in the driver’s seat of your organization’s security assessment process. You’ll be able to make smart decisions to lower risks.
Take Action Based on Findings
Your next move should hinge on the findings of your third-party risk assessment. Promptly addressing any issues and taking the right steps to lower potential risks is key to the success of your risk management program.
Here are four steps you might find helpful:
- Do a detailed analysis of the risks tied to each vendor. This will give you a clear picture of their risk to your business.
- Review the assessment results and decide how to lower the identified risks best. You might need to put extra controls in place or change how you bring on and vet new vendors.
- Stick to best practices when dealing with the risks you’ve found. This means setting clear policies and procedures for risk assessment, regularly reviewing and tweaking your risk assessment methods, and getting the right people involved.
- Don’t forget that assessing third-party risk isn’t a one-time thing. Keep an eye on how your vendors are doing and whether they’re sticking to the rules, carry out regular reviews, and stay in the know about any changes or new risks that might come up.
Let’s Talk About Supplier Risk Assessment: A Few Handy Tips
Having clear rules and guidelines for supplier risk assessment in your business is important. This is what keeps supplier risk assessment effective.
Regular supplier risk assessments help businesses spot potential risks. These could be a data breach, cyber threat, a hit to information security, or damage to your reputation.
Remember, a third-party risk assessment identifies specific risks, monitors them, and mitigates them to ensure that your business continues running smoothly. This is a critical part of your third-party risk management program. So, whether you conduct these assessments in-house or by an independent safety or cybersecurity professional, or use a thorough third-party risk assessment template. This will help standardize your vendor assessment process and improve the effectiveness of risk monitoring in your organization.
Also, remember that you may want to monitor new vendors and business partners as part of your ongoing third-party risk assessment. After all, potential third-party risks can come from any product or service provider, not just your current ones. So, stay vigilant, stay safe!
Compliance Manager GRC
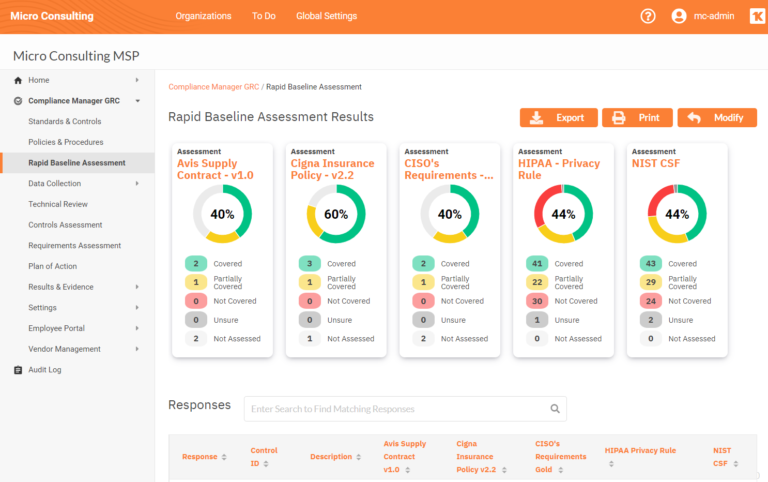
ZZ Servers provides an easy-to-manage tool called Compliance Manager GRC that your organization can use in its compliance process. This software is designed to manage various compliance assessment, management, and documentation tasks. It is a valuable tool for businesses wanting control over their compliance efforts.
With Compliance Manager GRC, you can start with a baseline risk assessment in less than an hour, collecting data on users, computers, and networks to validate compliance assumptions. The software also allows you to create customized policy and procedure manuals based on your unique workflows and track progress against every monitored standard or control set.
Product Specs:
- Purpose-built to manage compliance assessment, management, and documentation tasks
- Provides baseline risk assessment in less than an hour
- Collects data on users, computers, and networks for compliance validation
- Creates customized policies and procedures manuals
- Tracks progress against every standard or control set being monitored
Pros:
- Saves time and resources for your compliance tasks
- Provides a cost-effective solution for managing compliance
- Offers flexibility to manage multiple compliance standards simultaneously
- Includes value-added features for enhanced compliance management
- Highly customizable for unique workflows
Cons:
- It may require some initial setup and configuration
- Users may need some training to utilize all features fully
- It may not be suitable for organizations with complex compliance requirements
Guard Your Business with Third Party Risk Assessments
Your business’s success may depend on third-party risk assessments. Following the detailed process in this article and keeping a watchful eye with continuous monitoring and due diligence can shield your business from possible dangers.
However, having know-how and best practices alone is not enough to maintain successful partnerships. That’s where ZZ Servers can help. Our experienced team provides comprehensive solutions to address the challenges mentioned in this article. With our services, you can effectively manage and reduce third-party risks, ensuring the security and stability of your business.
Contact us today to learn how ZZ Servers can guide you through the twists and turns of third-party risk assessments. Our custom solutions, which include risk analysis, continuous monitoring, and other compliance and IT Management services, will offer you the reassurance you’re looking for. Don’t let potential threats jeopardize your business. Take charge and safeguard your future with ZZ Servers.



