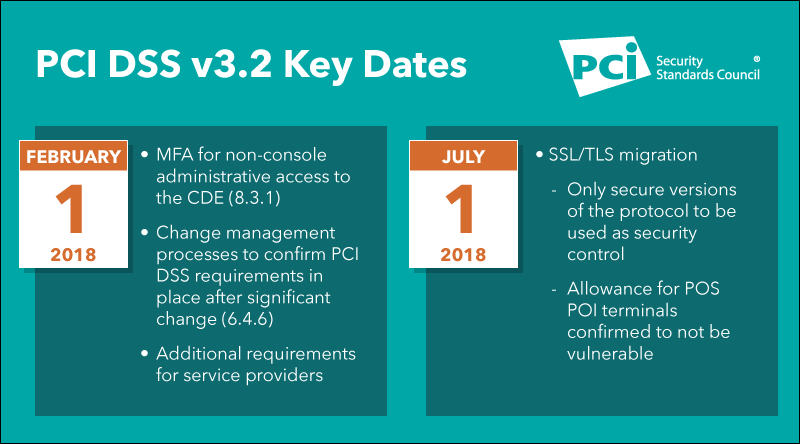
With widespread and disastrous SSL/TLS vulnerabilities taking place such as POODLE and FREAK, SSL and early TLS versions are no longer considered strong cryptography and any web site that still uses them is insecure.
According to the new rules in PCI DSS v3.1, companies have until June 30, 2016 to update to a more recent version of TLS (1.1 or higher). Prior to this date, existing implementations using SSL or an early TLS must have a formal risk mitigation and migration plan in place.
The PCI DSS v3.1 requirements directly affected are:
-
- Requirement 2.2.3 Implement additional security features for any required services, protocols, or daemons considered insecure.
-
- Requirement 2.3 Encrypt all non-console administrative access using strong cryptography.
- Requirement 4.1 Use strong cryptography and security protocols to safeguard sensitive cardholder data during transmission over open, public networks.
ZZ Servers is here to help you meet these new requirements. We have tools and procedures in place to quickly implement required changes and help you maintain the security and compliance of your PCI infrastructure. Please contact your Account Manager as soon as possible so we can help you implement the required changes.