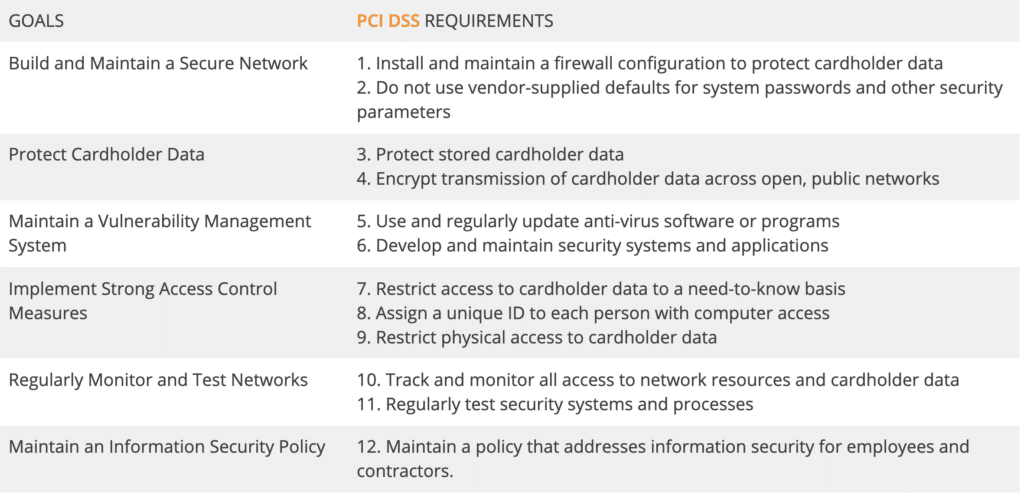
Payment Card Industry (PCI) compliance is growing in its rigor and scope amid the rapidly evolving world of online and mobile credit card transactions. The PCI Data Security Standards (PCI DSS) aim to protect consumer credit card data by offering businesses an outline of rules and guidelines to ensure their credit card systems are secure.
But the reality of implementing these standards is where the rubber meets the road for many businesses when they have to validate their processes and procedures through an annual PCI audit. Getting ready for a PCI audit is akin to training for a marathon. It takes months of preparation and hard work long before the day of the big event. Remaining compliant is like a marathon that never ends, needing focus 27-7-365.
It all starts with knowing your PCI environment; what kind of operating systems do you run, how many operating systems do you run, what policies do you have in place to manage those operating systems, how many staff and third-party vendors are involved in managing and maintaining those systems – and many more of those such questions must be answered.
The next step is to create or update your business’ network diagram. PCI compliance requires an accurate diagram that outlines system connections to card data. The diagram needs to show how cardholder data enters your network, which systems that data interacts with as it is processed within the network and at what points cardholder data may leave the network such as flowing to a payment processor. A Qualified Security Assessor (QSA) will want to be able to see exactly where and how card data flows through your networks, devices, system components and any connections between the cardholder network and other networks.
It’s also essential that the leadership of your business knows what to expect. If this is your first PCI audit, you might consider doing a pre-assessment with a QSA so that all stakeholders (i.e. head of security, head of compliance, head of operations, head of development, head of legal) understand the process and policies. At the very least, you should download the PCI DSS self-assessment questionnaire to give you and your team a starting to point for how to prepare. The questionnaire will prompt you to evaluate everything from which credit cards are accepted and the number of transactions per year to the number of firewalls and routers you have and how many external and internal IP addresses are in your network. The bottom line is that you need to know your system before you start the audit process.
Then there’s the looming uncertainty of whether your network and systems are in fact secure. Don’t be caught by surprise. PCI DSS requires an annual risk assessment that identifies critical threats and vulnerabilities. To meet this requirement it is best to conduct an internal examination of your systems, process and procedures and as well as a full risk assessment to determine system vulnerabilities prior to an audit. Then you can correct any errors and prioritize IT security enhancements based on any potential threats.
Preparing for an audit is a lot of work. There are a lot of security standards to meet and policies to implement. And you have to make sure your business’ practices match those policies. A third party vendor, such as ZZ Servers, can help with security measures like firewall controls, security standards, data encryption, log monitoring and log archiving. Before you get overwhelmed by the audit process, remember there is help out there that can help kickoff the process of preparing for an audit – saving time and stress along the way.