
Protecting Your Business from Data Theft
Hey there, fellow business owner! I want to talk to you about something that might not be on your radar but is absolutely crucial: cybersecurity. In today’s digital world, data theft is a real and growing threat to businesses of all sizes. And guess what? You might be more vulnerable than you think!
What is Data Theft?
Let’s start with the basics. Data theft occurs when cybercriminals use malware to steal sensitive information from your business. This malware, known as information stealers, can infiltrate your systems and snatch data stored in various applications like web browsers, email clients, and even gaming services. These sneaky thieves package the stolen information into something called ‘logs’ and either use it for malicious attacks or sell it on the dark web.
Surprising Impact on Businesses
Now, you might be thinking, “Why would cybercriminals target my business? I’m just a small fish in a big pond.” Well, here’s the thing: information stealers don’t discriminate. They primarily target careless internet users, but they can also have a massive impact on corporate environments like yours.
Here’s how it happens: Many employees use their personal devices for work or access personal stuff from their work computers. This seemingly innocent behavior can lead to devastating consequences. Info-stealer infections can easily snatch business credentials and authentication cookies, giving cybercriminals a direct ticket into your systems.
The Alarming Numbers
Don’t just take my word for it. According to a recent report by cybersecurity firm Flare, there are approximately 375,000 logs containing access to popular business applications. We’re talking about big names like Salesforce, Hubspot, Quickbooks, AWS, GCP, Okta, and DocuSign. These logs are like golden tickets for cybercriminals, granting them access to your sensitive data and systems.
Check out these jaw-dropping numbers from Flare’s research:
- 179,000 AWS Console credentials
- 2,300 Google Cloud credentials
- 64,500 DocuSign credentials
- 15,500 QuickBooks credentials
- 23,000 Salesforce credentials
- 66,000 CRM credentials
And that’s not all. There are approximately 48,000 logs containing access to “okta.com,” an enterprise-grade identity management service. That’s a lot of potential access points for cybercriminals!
Where Do These Logs Come From?
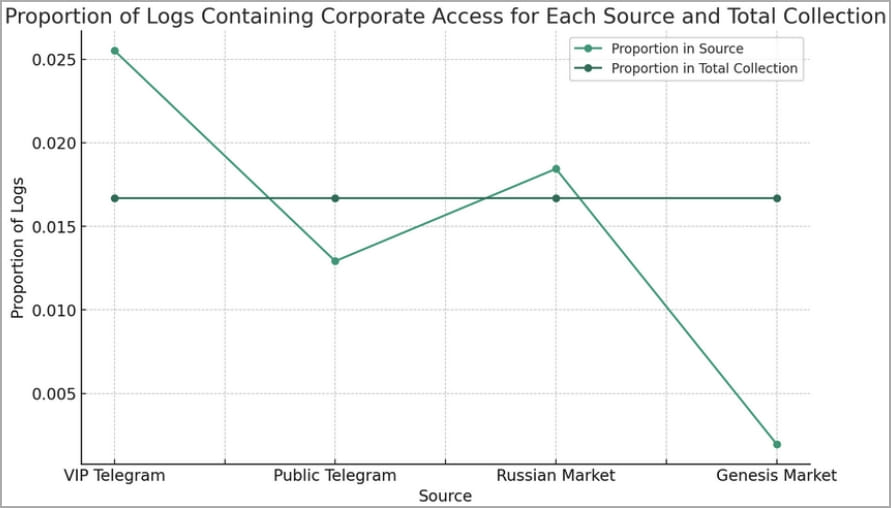
Now, you might be wondering, where do these logs even come from? Well, Flare’s research shows that a whopping 74% of these logs were found on Telegram channels. Another 25% were discovered on Russian-speaking marketplaces like the ‘Russian Market.’
This information is crucial because it tells us that cybercriminals are actively targeting businesses like yours. These logs containing corporate access were over-represented on these platforms, meaning that cybercriminals are specifically looking for valuable information from corporate environments.
The Risk of OpenAI Credentials
But wait, there’s more! Flare also discovered over 200,000 stealer logs containing OpenAI credentials. That’s twice the amount reported by Group-IB. Why is this important? Well, if cybercriminals get their hands on your OpenAI credentials, they can potentially access your proprietary information, internal business strategies, and even your source code. Yikes!
The Value of Corporate Credentials
Believe it or not, these corporate credentials are like gold in the cybercrime underground. They are considered “tier-1” logs because they provide direct access to critical systems and sensitive data. Cybercriminals can sell these logs on private Telegram channels or forums, such as Exploit and XSS, for a hefty profit.
With compromised credentials, cybercriminals can sneak into your CRMs, RDP, VPNs, and SaaS applications. And once they’re in, they can wreak havoc by deploying stealthy backdoors, ransomware, and other malicious payloads.
Protecting Your Business
Now, I don’t want to leave you feeling helpless and vulnerable. There are steps you can take to minimize the risk of info-stealer malware infections:
- Use password managers: Password managers can help you create strong, unique passwords for each of your accounts without the hassle of remembering them all.
- Enforce multi-factor authentication (MFA): MFA adds an extra layer of security by requiring multiple forms of verification, like a fingerprint or a unique code sent to your phone, to access your accounts.
- Set strict controls on personal device use: Make sure your employees understand the risks of using personal devices for work or accessing personal content on work computers. Establish clear rules and guidelines to protect your business.
Additionally, it’s crucial to educate your employees about common infection channels. Teach them how to identify and avoid malicious Google Ads, suspicious YouTube videos, and risky Facebook posts. By empowering your employees with knowledge, you’re strengthening your business’s defense against cyber threats.
Contact Us to Safeguard Your Business
Protecting your business from data theft is a top priority, and we’re here to help. At ZZ Servers, we specialize in cybersecurity and have the expertise to keep your business safe from these ever-evolving threats. Don’t wait until it’s too late. Reach out to us today to learn how we can assist you in safeguarding your business.


