In the ever-expanding digital landscape, security events and event logs play a critical role in maintaining the integrity and safety of computer systems. As organizations increasingly rely on technology for their day-to-day operations, monitoring, analyzing, and responding to security events becomes paramount.
The Significance of Security Events
Security events encompass a broad spectrum of incidents that have the potential to impact the confidentiality, integrity, or availability of information. These events range from unauthorized access attempts and malware infections to system crashes and hardware failures.
Importance of Security Events
Security events indicate potential security threats and vulnerabilities within a system. By monitoring these events, organizations can detect and respond to security incidents promptly, preventing or minimizing the impact of a breach. The proactive analysis of security events also aids in the continuous improvement of an organization’s cybersecurity posture.
Types of Security Events
Understanding the different types of security events is crucial for maintaining a robust security posture. Security events provide valuable insights that can help identify threats, detect anomalies, and ensure policy compliance. Let’s explore some key event categories and what they can indicate.
● Unauthorized Access Attempts: Event logs often show unauthorized access attempts when an individual or system tries accessing a network, system or application without proper authorization. Details like IP addresses, usernames and timestamps help pinpoint potential attackers.
● Malware Infections: Malware events signal the detection of viruses, trojans, ransomware and other malicious software. Logs reveal affected systems, malware types and security response actions to contain threats.
● Denial of Service (DoS) Attacks: DoS attacks aim to overwhelm systems with abnormal traffic volumes, disrupting normal functions. Related logs exhibit unusual network patterns, aiding security teams seeking to implement mitigations.
● Security Policy Violations: Deviations from established policies, like unauthorized configuration changes or bypassing controls, violate security guidelines. Event logs specify the nature of violations and identities of those involved.
● Anomalous User Activity: Monitoring for unusual patterns in user actions, such as frequent file access or privilege escalation, helps uncover potential insider threats. A trail of user behaviors facilitates thorough analysis.
● Changes to System Configurations: Unauthorized configuration changes can compromise integrity or introduce vulnerabilities. Timely review of associated logs maintains a stable, secure environment.
● Data Breaches: Breaches involve unauthorized data access, acquisition or disclosure. Logs from such incidents provide clues about accessed information, methods used and duration to expedite response and mitigation efforts.
By diligently reviewing security events across these categories, organizations can proactively safeguard their environments, respond rapidly to incidents and help ensure ongoing compliance. Don’t hesitate to leverage your security team for any additional protection needs.
The Role of Event Logs
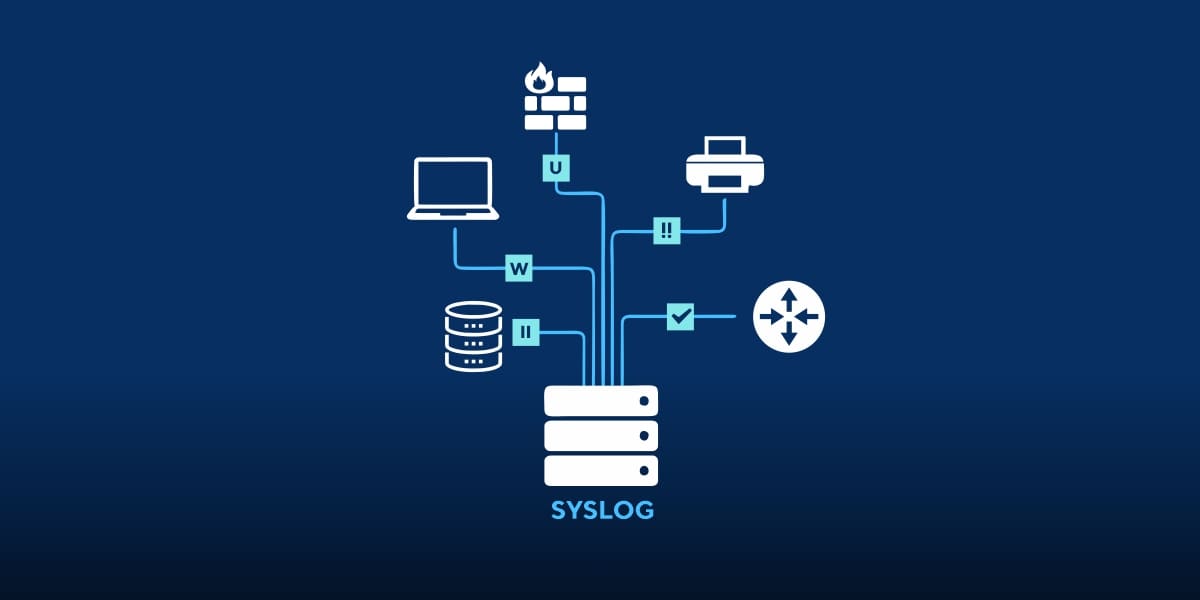
Maintaining comprehensive event logs is integral for effective security management and response. Let’s explore their key functions. Event logs objectively document a system’s activities, errors and security-related events over time. This chronological record facilitates important oversight.
● Types of Event Logs: Logs are categorized by the data captured. Common varieties include security logs for authentication and access events, system logs detailing operations and warnings, and application logs tracking specific software components.
● Key Log Elements: Each entry contains salient details like a unique identifier, timestamp of occurrence, originating source, associated user account, and descriptive information. These elements enable meaningful analysis.
● Event Log Analysis: Leveraging Security Information and Event Management systems allows centralizing log collection and automated multi-source investigation. This powerful approach helps uncover patterns, anomalies and threats through contextual insights.
● Incident Response Aids: Should issues arise, event logs play a vital role. Their timeline of activities aids in understanding an event’s nature, scope and tactics. This informs containment and remediation best practices to minimize future disruptions.
Overall, properly harnessing these chronicles of system functions and security-related occurrences is pivotal for proactive protection and swift, targeted response when needed. Don’t hesitate to contact me for any log management recommendations to strengthen your security posture.
Best Practices for Security Event Management
Effectively managing security events is essential for maintaining robust cyber defenses. Adopting best practices in this area helps ensure prompt detection, containment and remediation of threats to minimize disruption. Some key guidelines include:
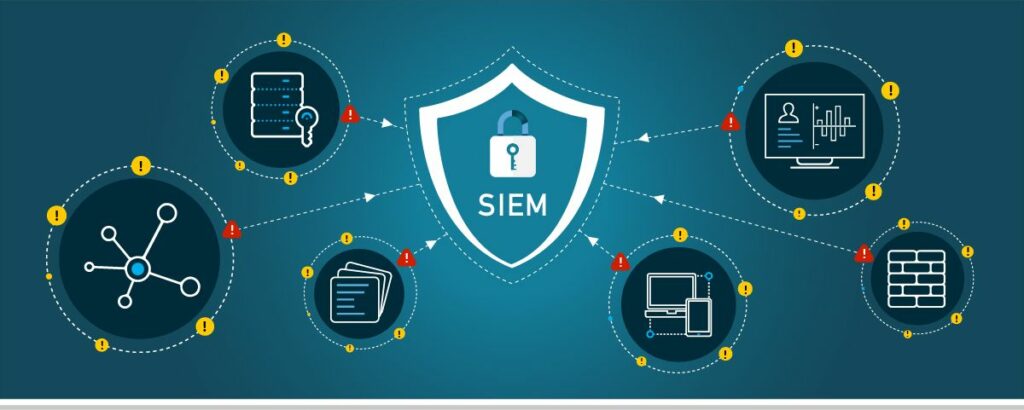
● Regular Log Reviews: Regularly reviewing event logs is essential for identifying security incidents on time. Automated tools can assist in parsing and analyzing logs, but human oversight is crucial for contextualizing events and understanding the broader security implications.
● Correlation of Events: Correlating events from multiple sources enhances the accuracy of threat detection. SIEM systems use correlation rules to identify patterns of behavior that may indicate a security threat. This approach allows organizations to move beyond isolated events and understand the context of potential incidents.
● User Training and Awareness: User awareness is a critical component of security event management. Training users to recognize and report security incidents contributes to a more responsive and proactive security posture. Users should be educated on the importance of promptly reporting anomalies or suspicious activities.
● Automation of Response: Automated response mechanisms triggered by specific events can help contain and neutralize threats in real time. It includes blocking IP addresses associated with malicious activity or isolating compromised systems from the network. Automation reduces response time and minimizes the impact of security incidents.
● Regular System Audits: Regular audits of system configurations, access controls, and security policies ensure the environment remains secure. Audits contribute to the early detection of unauthorized changes and vulnerabilities, allowing organizations to address issues before they can be exploited.
● Secure Storage of Event Logs: To maintain the integrity of event logs, it is crucial to store them securely. Protecting logs from unauthorized access or tampering ensures their reliability for forensic analysis. Secure storage also involves implementing measures to prevent log data’s accidental deletion or loss.
Strengthen Your Cyber Defenses with ZZ Servers
If the types of security events and best practices for event log management discussed in this article have you recognizing areas for improvement within your own organization’s cybersecurity program, consider partnering with ZZ Servers – an experienced managed security services provider. For over 17 years, our team of experts has helped businesses just like yours proactively monitor and analyze security logs to detect threats, respond rapidly to incidents, and ensure ongoing compliance. Contact us today at 800-796-3574 to discuss a customized security event management solution tailored to your unique needs and budget. Our proven processes and personalized approach will help elevate your defenses against evolving cyber risks.
Frequently Asked Questions
u003cstrongu003eWhat are some standard security events organizations should monitor closely?u003c/strongu003e
Some critical security events to prioritize include unauthorized access attempts, malware infections, abnormal user activity, changes to system configurations and data breaches. These events can indicate active threats or vulnerabilities and warrant timely analysis for mitigation. Monitoring various event types helps gain a holistic view of potential risks.
u003cstrongu003eHow can organizations classify different types of event logs?u003c/strongu003e
Event logs are commonly classified based on the source of events – such as security, system, application and network logs. This segmentation aids in a focused review of time-sensitive security-related logs. Critical assets or user groups can also filter logs to contextualize events. Proper classification streamlines analysis across diverse log sources.
u003cstrongu003eHow can organizations analyze logs at scale?u003c/strongu003e
Leveraging security information and event management (SIEM) solutions is common practice to aggregate, normalize, index and correlate logs from multiple sources at high volumes. SIEMs also facilitate automated log parsing, querying, alerting and visualization capabilities to detect anomalies. Their correlation engines assist in identifying relationships between isolated events and indicators of potential incidents.
u003cstrongu003eWhat are some best practices for event log management?u003c/strongu003e
Key areas to focus on include centralized log collection, segmentation by criticality, compliant retention policies, access controls, configuration of alerts, audit logging, log protection measures and applying analytics techniques. Adopting industry-recognized frameworks like the MITRE ATTu0026amp;CK framework also aids in mapping detected behaviors to known threat tactics and courses of action.
u003cstrongu003eHow should organizations respond to security incidents?u003c/strongu003e
When incidents occur, timely analysis of relevant event logs is paramount. Logs provide forensic evidence for understanding the scope, vector and impact. It informs containment and remediation procedures. Logs also aid in attributing activities to establish accountability and taking corrective actions. Lastly, lessons from each incident strengthen defenses through policy, configuration, training and technology improvements.