Each time your system is updated and upgraded, your business should assess the threat to its network. Vulnerability scanners are an effective way of identifying devices on your network that are open to known and potential vulnerabilities.
What is Vulnerability Scanning?
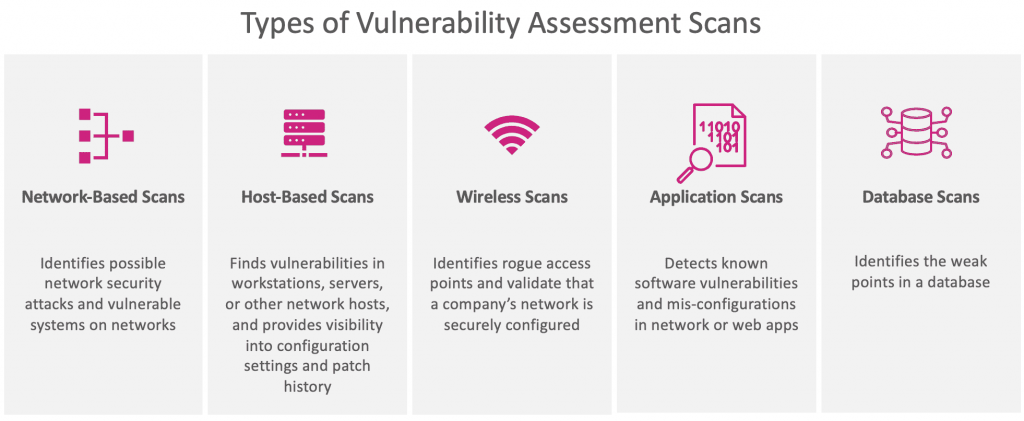
A vulnerability scan is exactly what it sounds like: a software program that compares a company’s operating systems, networks and applications against proprietary or public databases of known vulnerabilities. There are two types of scans: internal and external. An external vulnerability scan searches for holes in a network’s from the internet. An internal scan operates inside a business’ firewalls to assess real and potential vulnerabilities within the network.
Vulnerability scans provide reports on detected gaps in security and recommendations for security patches or vendor solutions. A report will also describe the types of vulnerabilities or risks found and a potential cause for each vulnerability. In accordance with the PCI Security Standards, scans assign vulnerabilities a numeric rating of 1-5. Those ratings are defined as follows:
- Level 1 – low risk where hackers can obtain information on configuration.
- Level 2 – medium risk where hackers can obtain sensitive configuration information.
- Level 3 – high risk where a hacker could conduct directory browsing or a limited exploit of read.
- Level 4 – critical risk including potential Trojan horses and file read exploits.
- Level 5 – urgent risk including confirmed Trojan horses, files read and write exploits and remote command execution.
The critical difference between a vulnerability scan and a penetration test, another security measure required under PCI standards, is that one is active and one is passive. Vulnerability scans assess the potential for risk using automated tools, while in a penetration test an IT professional actively tests a network’s defenses through manual exploitation. Both measures help ensure maximum data security.
What it means
So what does a vulnerability scan really tell you? It gives you a precise look at all identified vulnerabilities, and potential vulnerabilities, that are often only targeted by hackers.
Business learn through vulnerability scanning about the consequences and risks involved with each identified vulnerability and proposed actions to close security gaps. Think of it like a required physical. A person can’t take action to improve his health until he knows what’s wrong. It takes a doctor to identify early signs of health risks, much like it takes a vulnerability scan to assess silent IT threats.
ZZ Servers Vulnerability Scanners are designed to help merchants successfully comply with PCI data security guidelines. ZZ Servers can customize its scanning service, including internal and external network scans, to meet the specific needs of any business. Our automated remote probe uses a signature database of more than 3,500 vulnerabilities to assess the risk to your business. We provide web-based reports delivered securely to any web browser, and we offer recommendations and consultation for remediation of vulnerabilities.
Has your network had a check-up lately?
Sources:
http://www.isaca.org/Journal/archives/2014/Volume-4/Pages/Ethical-Hacking-The-Next-Level-or-the-Game-Is-Not-Over.aspx
https://www.pcisecuritystandards.org/pdfs/pci_scanning_procedures_v1-1.pdf
https://www.pcicomplianceguide.org/internal-vs-external-vulnerability-scans-and-why-you-need-both/
https://www.pcisecuritystandards.org/documents/Penetration_Testing_Guidance_March_2015.pdf