Hey there, fellow business owner! We’ve got some eye-opening news to share with you today. It seems that Taiwanese networking equipment manufacturer D-Link recently fell victim to a data breach. Yeah, it’s a big deal, and we’re here to break it down for you.
So, here’s what went down: some cybercriminal managed to infiltrate D-Link’s network and steal some seriously sensitive information. We’re talking about source code for D-Link’s D-View network management software, along with millions of customer and employee records. And get this—they even got their hands on the CEO’s details. Yikes!
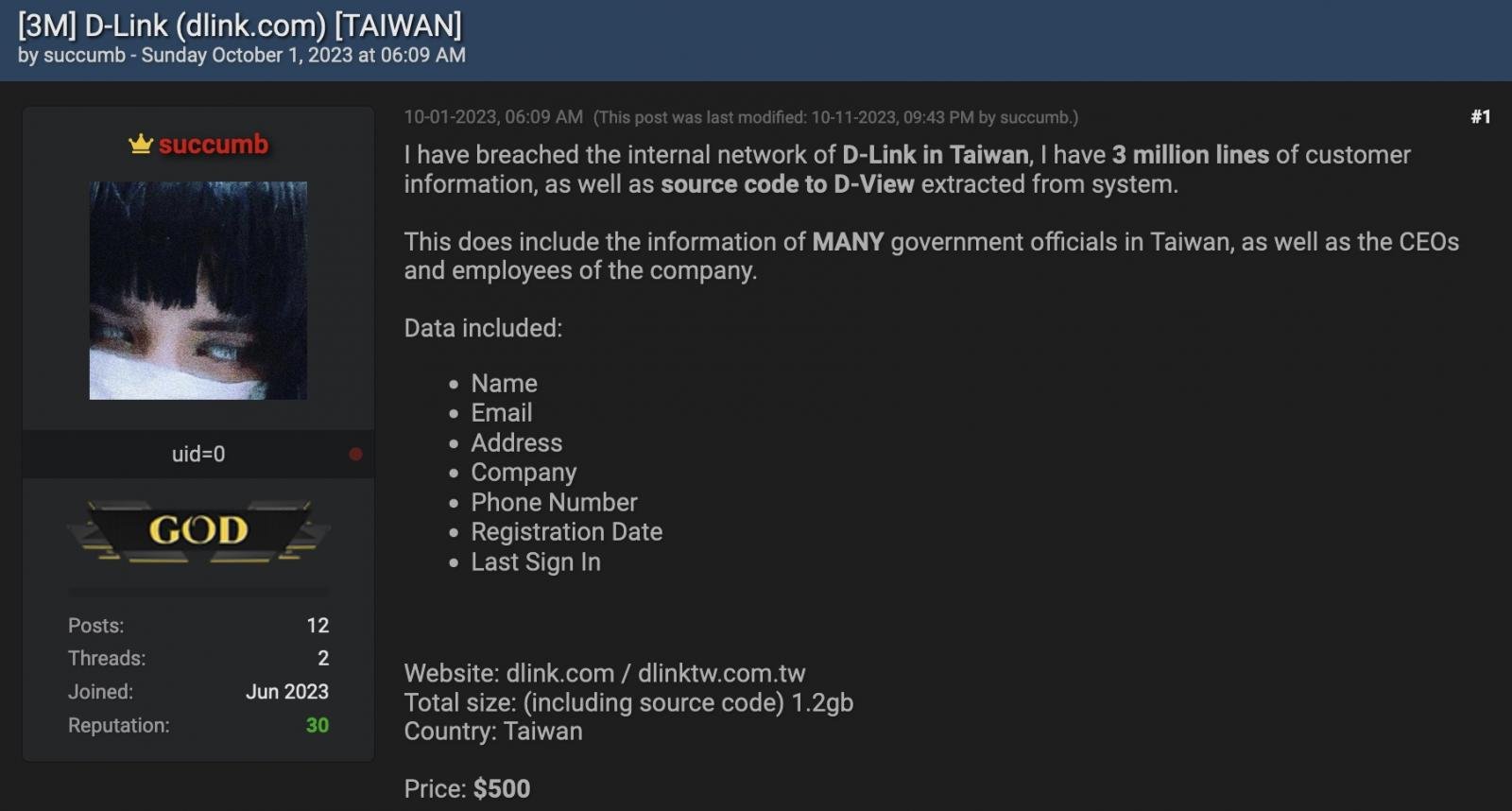
The stolen data includes personal information like names, emails, addresses, phone numbers, account registration dates, and the users’ last sign-in dates. It’s a treasure trove of valuable info, and it’s out there in the wild.
But hold on a sec—before you panic, let’s dive deeper into the details. The cybercriminal provided samples of 45 records, and it turns out they’re from way back in 2012 and 2013. Yeah, that’s right, they’re ancient! So, while it’s still a breach and a breach is never good, it’s important to note that the data isn’t as fresh as it might seem.
According to the attacker, they’ve got a whopping 3 million lines of customer information, including some high-profile government officials in Taiwan and the hardworking folks at D-Link. And guess what? They’re actually selling this stolen data on a hacking forum for a cool $500. It’s like a cyber black market out there.
How did this happen?
Now, you might be wondering, how on earth did D-Link let this breach happen? Well, it turns out that one of their employees fell for a phishing attack. You know, those sneaky emails that trick you into giving away sensitive info? Yeah, that’s the one.
As soon as D-Link discovered the breach, they sprang into action. They shut down the servers that were potentially affected and disabled most of the user accounts while they investigated what went wrong.
Here’s the thing, though—the breach happened in a “test lab environment” that used an outdated system called D-View 6. This system has been out of commission since 2015, so you’ve got to wonder why it was still up and running. It’s a head-scratcher, for sure.
But here’s the good news: D-Link says that only around 700 records were compromised, and those records have been inactive for at least seven years. Plus, the majority of the data isn’t super sensitive. Phew!
There’s another twist to this story, though. D-Link suspects that the cybercriminal messed with the login timestamps to make it seem like the breach was more recent than it actually was. Sneaky, right?
Oh, and here’s something else to keep in mind—D-Link believes that most of its current customers won’t be affected by this incident. So, if you’re a D-Link customer, take a deep breath and relax a little.
Now, we know this whole situation might make you feel a bit uneasy. It’s natural to worry about your own business’s cybersecurity. That’s where we come in.
Are Hackers Responsible for the Potential Infiltration of Voter Rolls?
Are hackers responsible for the potential voter roll infiltration by hackers? This contentious question raises concerns about the security of our democratic process. With sophisticated cyber attacks becoming increasingly common, experts worry about hackers gaining unauthorized access to voter rolls, potentially compromising voter data and casting doubt on the integrity of elections. Safeguarding these rolls is of paramount importance to protect the democratic rights of citizens and preserve the trust in our electoral systems.
How can ZZ Servers help you?
As experts in cybersecurity, we’ve seen it all. We know how important it is to protect your business from cyber threats, big or small. Whether you’re a small startup or a well-established company, we’ve got your back.
Our team of dedicated professionals is here to assess your current security measures and implement robust solutions tailored to your specific needs. We’ll help you stay one step ahead of the cybercriminals, so you can focus on what you do best—running your business.
Don’t wait until it’s too late. Contact us today to learn more about how ZZ Servers can assist you in safeguarding your business against cyber threats. Trust us, it’s a decision you won’t regret.



