As technology permeates every aspect of modern life and enterprise, the threat of cyberattacks has grown exponentially. Robust security measures are imperative to safeguard digital assets and infrastructure from malicious intrusions. A core component of any cyber defense strategy is an intrusion detection system (IDS), which monitors networks and systems for anomalous activity that could indicate a compromise. This article will explore the major types of IDS technologies available and how each approach uniquely enhances security posture.
Network-Based Intrusion Detection Systems
One of the most common varieties is a network-based IDS (NIDS). Functioning at the data link layer, an NIDS passively analyzes traffic passing through critical network points like routers, firewalls, and switches. Inspecting packet headers and payloads detects intrusion attempts from anomalies like policy violations, known exploits, and malware signatures. NIDS offers comprehensive visibility without relying on agents, making it well-suited for monitoring large, complex networks in real-time. Prominent commercial NIDS include Cisco Firepower and Juniper Stealthwatch. Open-source alternatives like Snort and Suricata are also widely deployed.
Host-Based Intrusion Detection Systems
While NIDS monitors the network perimeter, a host-based IDS (HIDS) protects individual systems and endpoints. Operating at the host layer, HIDS agents are installed on servers, workstations, and Internet of Things (IoT) devices to continuously scrutinize inbound/outbound traffic, system/application logs, and file integrity for signs of compromise. Any deviations from the system’s normal usage baseline that could indicate malware, policy violations or privilege escalation are flagged. Popular commercial HIDS products include OSSEC, Carbon Black Defense and CrowdStrike Falcon. For open-source use, Tripwire and Samhain are excellent options.
Wireless IDS/IPS
As more organizations adopt wireless networking for employee and visitor devices, ensuring Wi-Fi security is paramount. Wireless intrusion detection and prevention systems (WIDS/WIPS) monitor wireless network traffic and analyze radio patterns to detect potential threats like rogue or unauthorized access points attempting to intercept communications. WIDS can also identify malicious clients probing the SSID or MAC spoofing attempts. Advanced WIPS solutions offer automated protection by preventing suspicious wireless devices from connecting entirely. With remote and mobile workforces relying on Wi-Fi, WIDS/WIPS are indispensable for maintaining wireless perimeter security.
Physical IDS
Physical security also demands holistic monitoring as operational technology expands beyond digital systems. Video surveillance analytics integrate with IDS to recognize unusual movements, loitering or unauthorized access near assets. Environmental sensors feeding data to IDS can identify anomalies indicating sabotage of industrial processes. Where electronic access controls govern entry points, IDS correlate badge swipes with other physical events to flag tailgating or unauthorized extended access. Integrating physical security tools like intrusion panels with network IDS via platforms like Security Information and Event Management (SIEM) provides a unified view of digital and physical threat activities within smart buildings and critical infrastructure environments.
IDS for OT Networks
Industrial control systems demand dedicated IDS due to unique performance and safety requirements. OT-IDS monitor industrial internet-of-things devices, engineering workstations, HMIs and field controllers for unauthorized configuration changes, process command injections or communication disruptions that could enable physical sabotage. They also inspect industrial protocols for malformations indicating potential compromise. With OT networks increasingly connected to IT infrastructures and remote access prevalent, OT-IDS is a vital safeguard against cyberattacks that could endanger equipment, personnel and facilities. Regular IDS updates ensure continued detection of new vulnerabilities specific to industrial ecosystem technologies and systems.
IDS for Containers
Dedicated container security solutions are needed as applications migrate to cloud-native microservices architectures relying on containers. Lightweight container IDS integrates into container orchestration platforms to monitor workloads deployed across hybrid and multi-cloud infrastructures for known vulnerabilities, unusual resource consumption and lateral movement risks. They automate threat detection and remediation without disrupting application portability or performance. With containers increasing rapidly at the edge and across serverless environments, container-aware IDS assume increasing importance to protect dynamically scheduled functions and services from modern attack techniques.
Network Behavior Analysis

Network behavior analysis (NBA) is a relatively new development, which functions at the application layer to detect even stealthier lateral movement threats. Leveraging machine learning, NBA establishes a comprehensive baseline of everyday network communications and user behaviors. It then identifies anomalies that deviate from expected patterns, like abnormal data transfers, suspicious login origins or usage outside typical work hours that could signal account takeovers or data exfiltration. Cutting-edge NBA solutions are gaining prominence, with Darktrace, Vectra and Varonis among the leaders.
Intrusion Detection Systems in Practice
In practice, a holistic IDS deployment incorporates multiple complementary techniques. For example, a NIDS monitors the perimeter while HIDS agents on hosts identify internal threats. User and entity behavior analytics (UEBA) track anomalous user actions. IDS data is aggregated into security information and event management (SIEM) systems for correlation, yielding deeper threat insights across networks, endpoints and user activities. Together, layered IDS strategies maximize visibility and the ability to detect sophisticated, multi-stage intrusions that individual products may miss. Regular maintenance, like signature/model updates, ensures optimal long-term efficacy.
Challenges and Mitigations
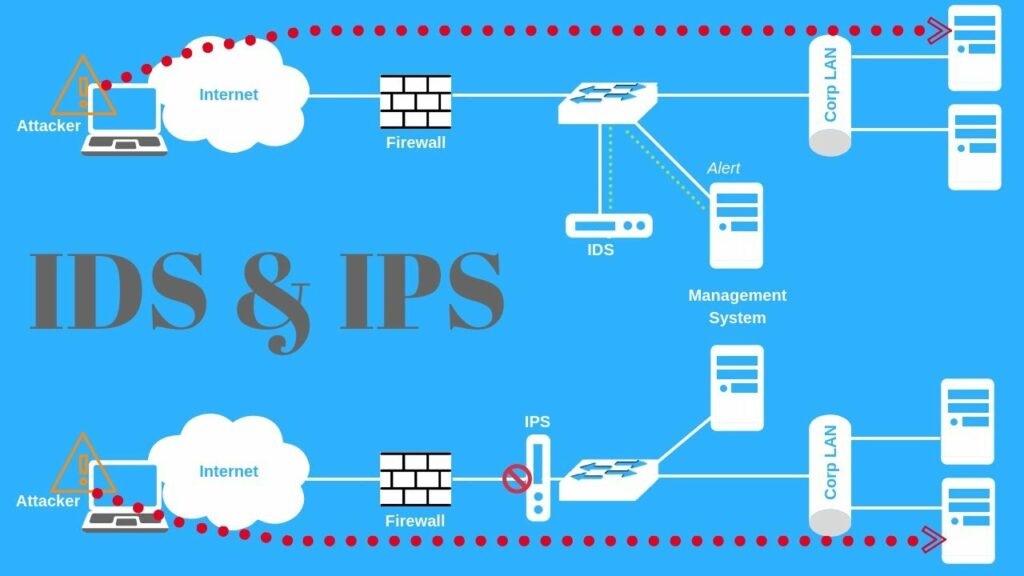
While IDS provides robust defenses, some challenges exist. High false positives and false negatives can occur without machine learning-assisted tuning. Volumetric attacks may overwhelm signature-based NIDS. Network-based IDS are often paired with inline intrusion prevention systems (IPS) capable of automatically blocking malicious traffic. Stealthy, encrypted threats may also bypass deep packet inspection NIDS. Here, HIDS, UEBA and behavioral analytics compensate by monitoring activities within compromised systems. The proper deployment also prevents evasion through traffic mirrors, switches configured for port spanning or network taps.
Future Directions
Looking ahead, the convergence of technologies is enhancing IDS. For example, next-gen firewalls (NGFW) integrate IDS/IPS, application controls and advanced malware protection. Host-based IDS leverage endpoint detection and response (EDR) capabilities for post-intrusion investigation and automated remediation. As 5G networks and edge computing proliferate, specialized IDS will emerge to safeguard these environments. Quantum computing also promises to accelerate machine learning-driven IDS through faster pattern matching and anomaly detection at scalAs as attack surfaces expand; continued innovation will strengthen intrusion monitoring via converged, autonomous and self-learning IDS architectures.
Strengthen Your Cyber Defences with ZZ Servers
As threats continue evolving rapidly in today’s digital landscape, don’t risk your organization falling victim to costly cyber incidents. Leverage ZZ Servers’ deep expertise in deploying optimized intrusion detection strategies since 2005. Our team of certified security analysts can design a tailored IDS solution to monitor your unique networks, systems and users – from procurement and installation to ongoing management and response training. Contact us today at 800-796-3574 to schedule a security assessment. Discuss your detection and prevention needs with a trusted advisor focused on delivering documented results through established processes emphasizing trust and accountability.
Conclusion
In summary, intrusion detection systems are vital in contemporary cybersecurity ecosystems. Diverse IDS categories like network-based, host-based and network behavior analysis offer layered defenses tailored for monitoring networks, systems and user behaviors. When deployed strategically with complementary solutions, IDS maximizes visibility and the ability to identify even stealthy multi-stage intrusions. Continued convergence with related technologies will further strengthen these critical monitoring tools. Looking ahead, specialized IDS adapted for emerging domains will assume growing importance as attack surfaces expand in our increasingly connected world.
Frequently Asked Questions
u003cstrongu003eWhat are the critical differences between network-based IDS and host-based IDS?u003c/strongu003e
Network-based IDS passively monitors network traffic at critical points, while host-based IDS involves installing agents on individual systems to scrutinize local activities and attributes. NIDS provides comprehensive perimeter visibility without relying on agents, whereas HIDS detects internal threats and ensures endpoint protection.
u003cstrongu003eHow do I choose the proper IDS for my organization?u003c/strongu003e
Consider factors like network size, complexity, regulatory u003ca class=u0022wpil_keyword_linku0022 href=u0022https://www.zzservers.com/services/managed-compliance/u0022 title=u0022complianceu0022 data-wpil-keyword-link=u0022linkedu0022u003ecomplianceu003c/au003e needs and budget. Evaluate both commercial and open-source options. Trial products to verify fit and scalability. Layer NIDS, HIDS and specialized IDS for a holistic defense tailored to your unique environment and risk profile.
u003cstrongu003eCan IDS prevent intrusions, not just detect them?u003c/strongu003e
While IDS primarily function as detection tools, network-based intrusion prevention systems (IPS) can automatically block malicious traffic when paired with IDS. Some advanced IDS also facilitate automated remediation. Integrated solutions combining IDS, firewalls, and endpoint protection are recommended for prevention needs.
u003cstrongu003eHow do I mitigate IDS evasion techniques?u003c/strongu003e
Deploy IDS strategically using techniques like port mirroring, inline network taps or switches configured for port spanning to prevent blind spots. Consider HIDS, UEBA and behavioural analytics to monitor activities within compromised systems bypassed by encryption or advanced evasion. Regular signature/model updates also strengthen the detection of new evasion tactics.
u003cstrongu003eWhat level of skills/resources are required to manage IDS?u003c/strongu003e
IDS management complexity varies by solution and deployment scale. Commercial IDS demand less expertise but higher costs. Open-source IDS involve steeper learning curves with support from robust communities. Allocating dedicated security analysts and periodic training ensures IDS remains optimized over time. Outsourcing IDS management to MSSPs is also an option.



